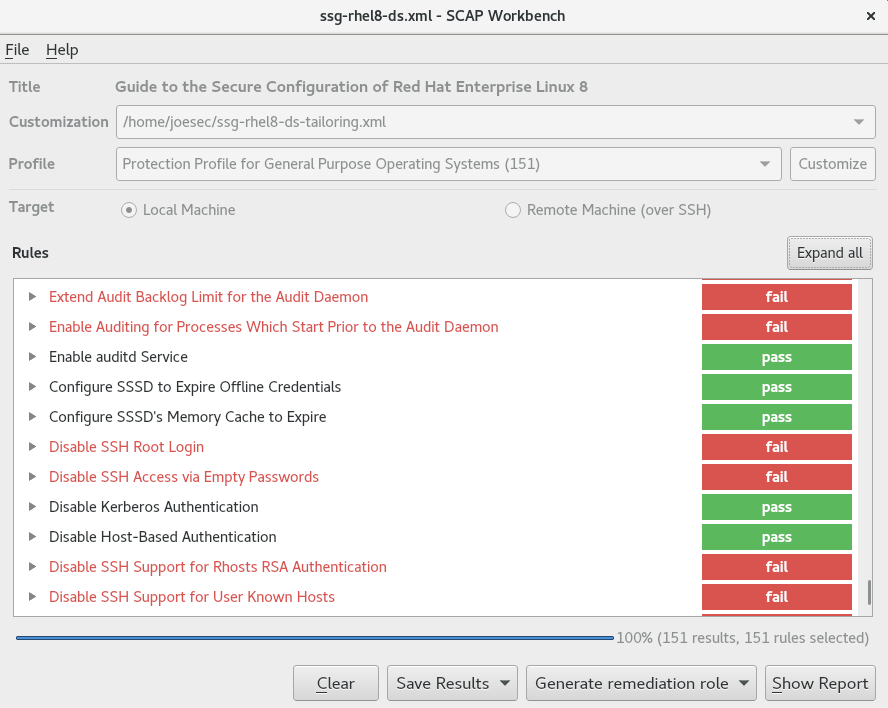
Chapter 9. Scanning the system for configuration compliance and vulnerabilities Red Hat Enterprise Linux 8 | Red Hat Customer Portal
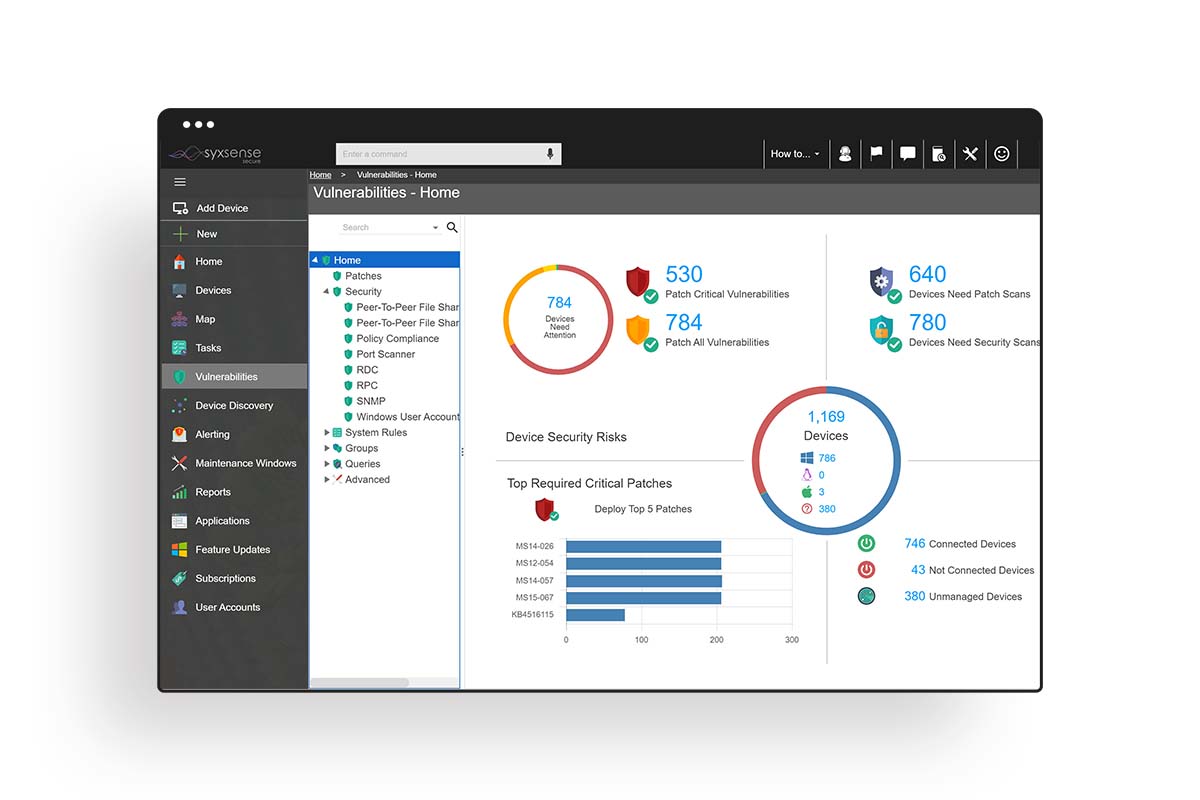
Syxsense Secure First to Unify Patch and Configuration Management with Vulnerability Scanning - Cybersecurity Excellence Awards

Qualys FreeScan service expanded with vulnerability scanning and configuration auditing - Help Net Security